Advantages of targeted attack protection solutions
Since the existing cybersecurity systems are based on known attacks and predict the prevention of only static threats, there is a need for a different system to cope with advanced targeted attacks.
Dynamics
Prevention
Comprehensive protection
Comprehensive protection
In order to ensure a comprehensive protection against advanced targeted attacks, set up a system to exchange detected data, which stops attacks at their source. This way you can control the three key attack vectors, i.e. email, web traffic and end stations. The system exchanges the detected data and stops attacks at their source.
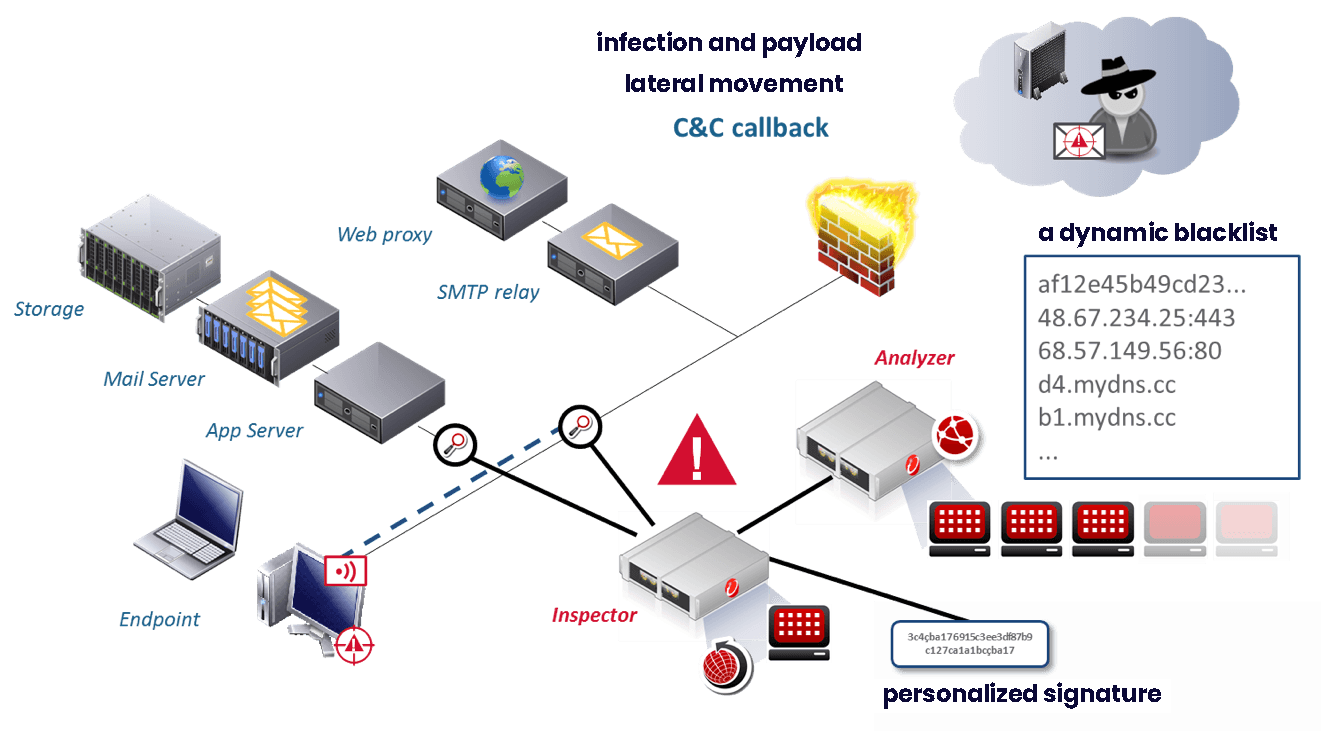
The course of a targeted attack
An advanced targeted attack against an information system takes place in several stages.
Gathering information about a potential victim
Finding the network entry point
Establishing connection from the victim's computer to the Internet
Engaging in the network lateral movement
Discovering resources and data
Data theft
Protect the information system against targeted attacks
Are you wondering which solution is right for you? Our cybersecurity experts can help you.
Why opt for our team?
Reasons to entrust us with the establishment of mechanisms designed to protect your information system against targeted attacks
A team of cybersecurity experts
Integration
We have been establishing and integrating
ICT solutions to enhance cybersecurity for over three decades.