A set of advanced solutions
Today, the protection of virtual environments is very important as most services are moved into virtual environments or a cloud. It is therefore imperative to introduce technological solutions designed to protect both data and the virtual environment in terms of cloud services.
Virtual environment protection solution with adequate firewalls
The solution is designed to install firewalls into a virtual environment with full functionality, which enable the NGFW services (IPS, APPFW, NAT, UTM, etc.).
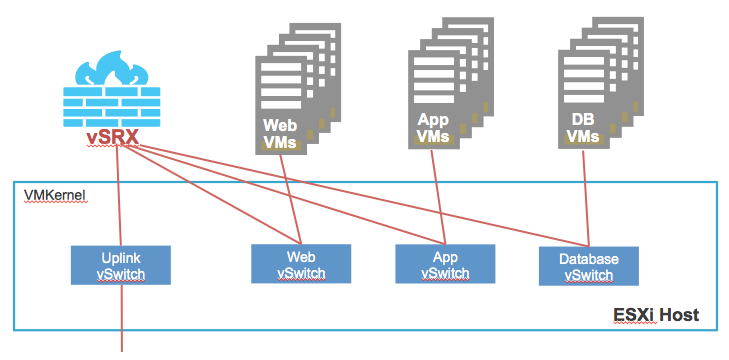
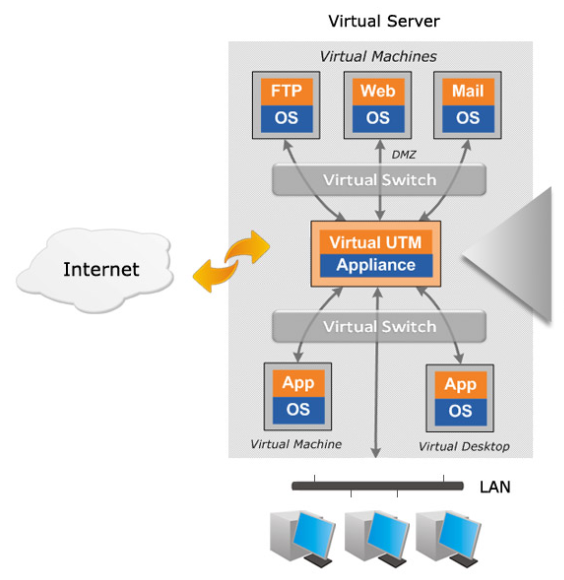
Protect your virtual environment with adequate firewalls
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
A file overview solution in an isolated environment
Files (attachments, files retrieved from the Internet) are scanned and checked for malicious code in an isolated environment using a cloud-based solution.
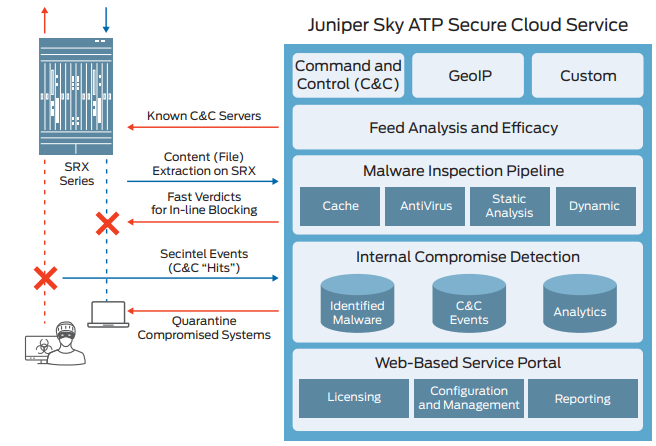
Protect your virtual environment with a file overview solution
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Next-generation virtual firewall solutions
Virtual firewalls are installed into the Docker with full functionality, which enables the NGFW services (IPS, APPFW, NAT, UTM, etc.).
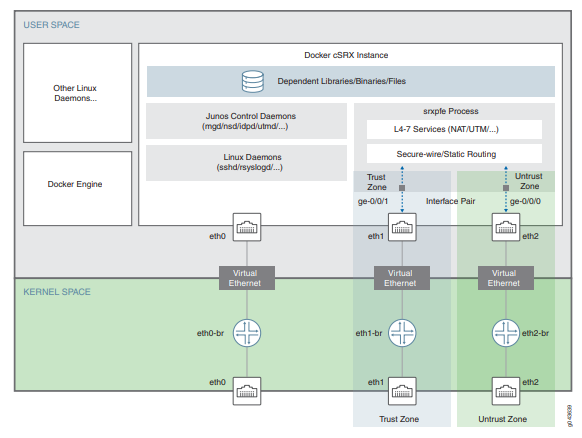
Protect your virtual environment with a virtual firewall solution
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Web application security and integrated authentication solutions
Virtual application barriers and systems guaranteeing a secure connection to public cloud services provide user authentication (SSO), DNS services, DDoS protection, traffic balancing between server infrastructure (Load Balancing), etc.
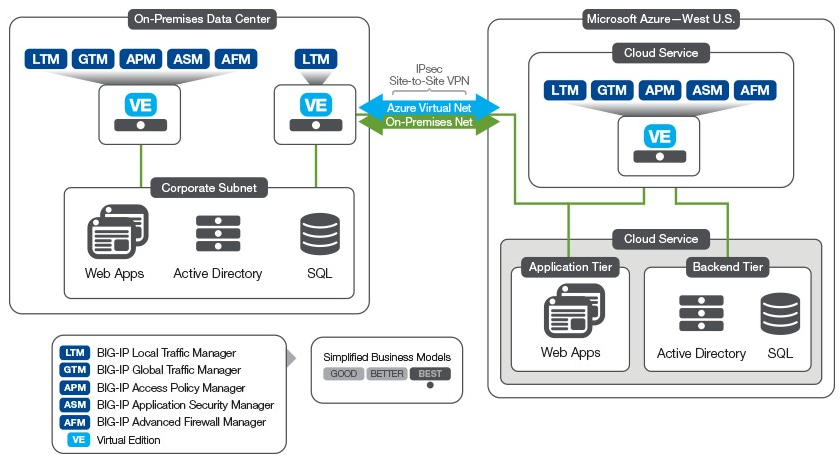
Establish web application security solutions with integrated authentication
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
The solution guaranteeing a secure internet access and traffic control
The solution guaranteeing secure Internet access also allows granular access control. The solution simultaneously enables the SSL decryption and anti-virus scanning for all sessions.
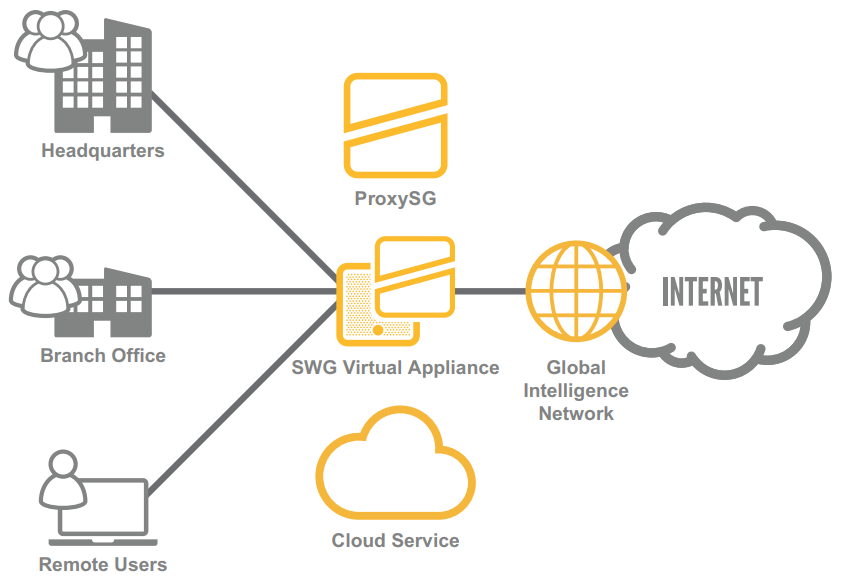
Protect your virtual environment with secure internet access
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Routing solutions for virtual environments
Routing solutions designed for virtual environments allow a full router functionality combined with the completely supported services.
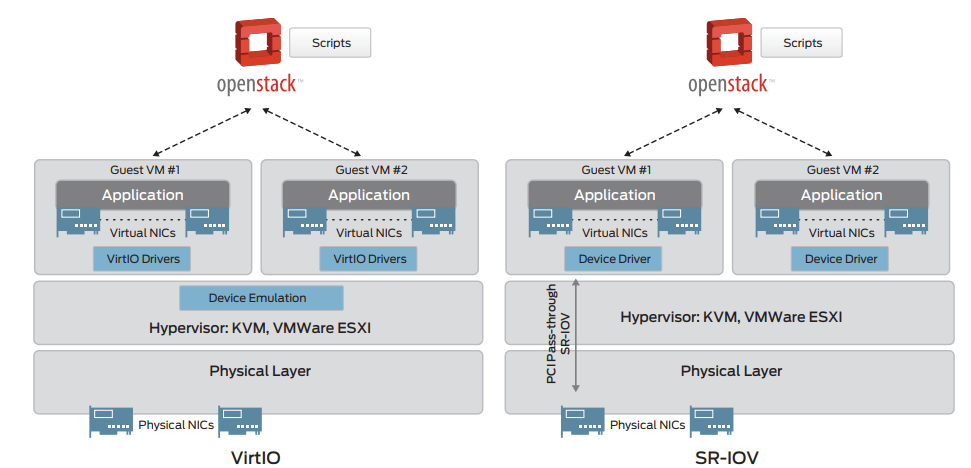
Implement a virtual environment routing solution
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Solutions designed for a secure remote access to resources via the SSL protocol
Solutions designed for a secure access to company resources allow access control, user verification etc. At the same time, you can use profiles for different types of access and connections to public cloud services via the SSL secure protocol.
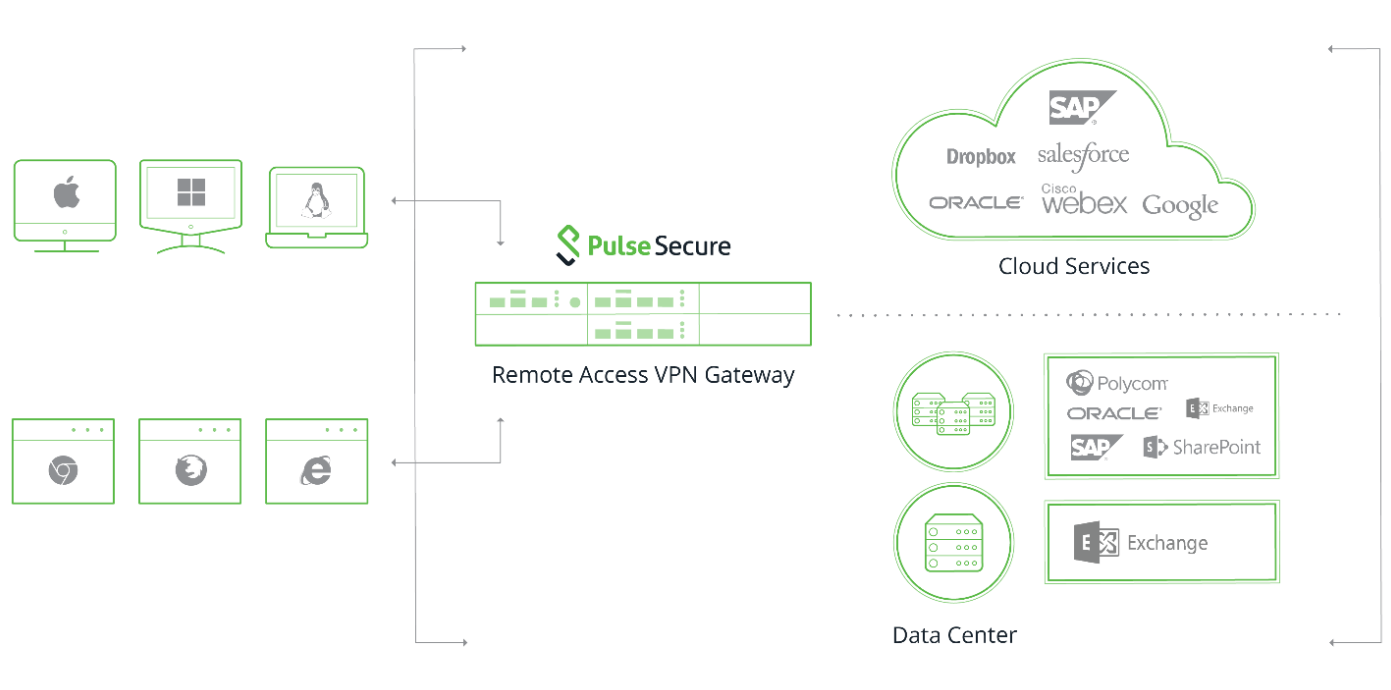
Implement a solution designed for secure remote access
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
The SIEM solutions
This log collection and correlation solution allows the reporting of unusual activities in the network from all devices and an overview of the network traffic flow, and performs forensics and traffic analysis.
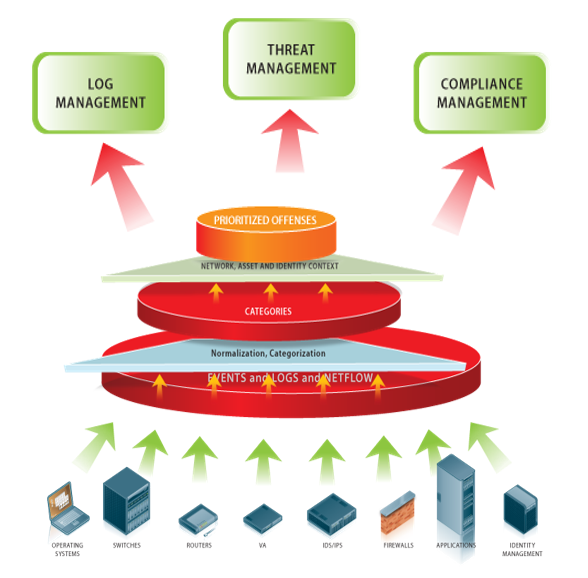
Implement an SIEM solution
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Privileged access management solutions
The privileged access management solution enhances cybersecurity by securing and protecting access to the most sensitive IT systems. The implementation of the solution ensures compliance with regulations such as the GDPR, NIS, PCI-DSS, HIPAA, ISO 27001, etc. By managing all accesses, we monitor activities and manage access passwords stored in the shared vault.
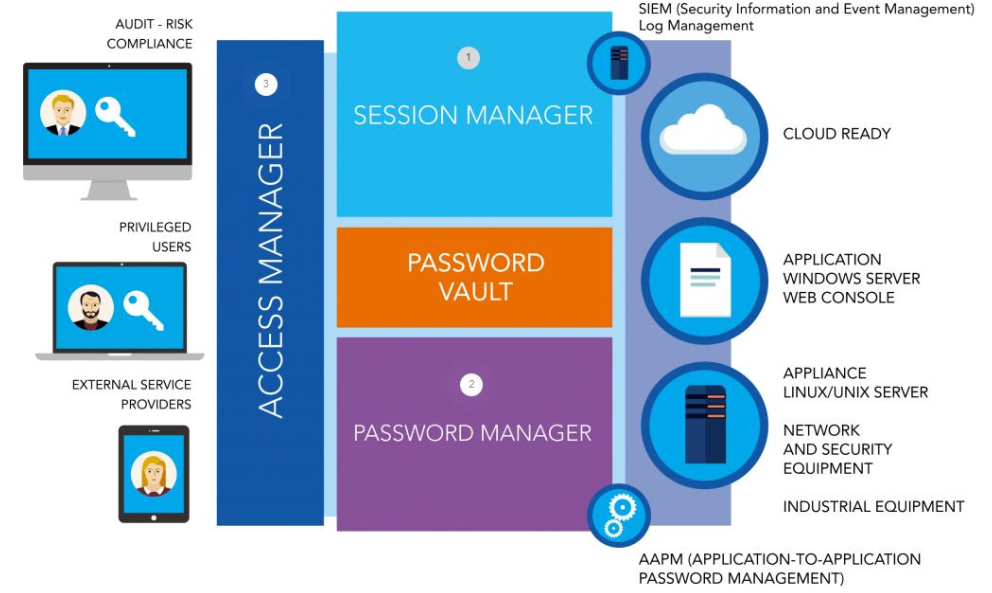
Establish a privileged access management solution
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Attack detection solutions using artificial intelligence and machine learning
The attack detection solutions using artificial intelligence and machine learning enable the detection of threats, anomalies and attacks in an IT or OT/ICS environment. The real-time solution detects network anomalies to prevent advanced attacks in the OT/ICS or IT environment.
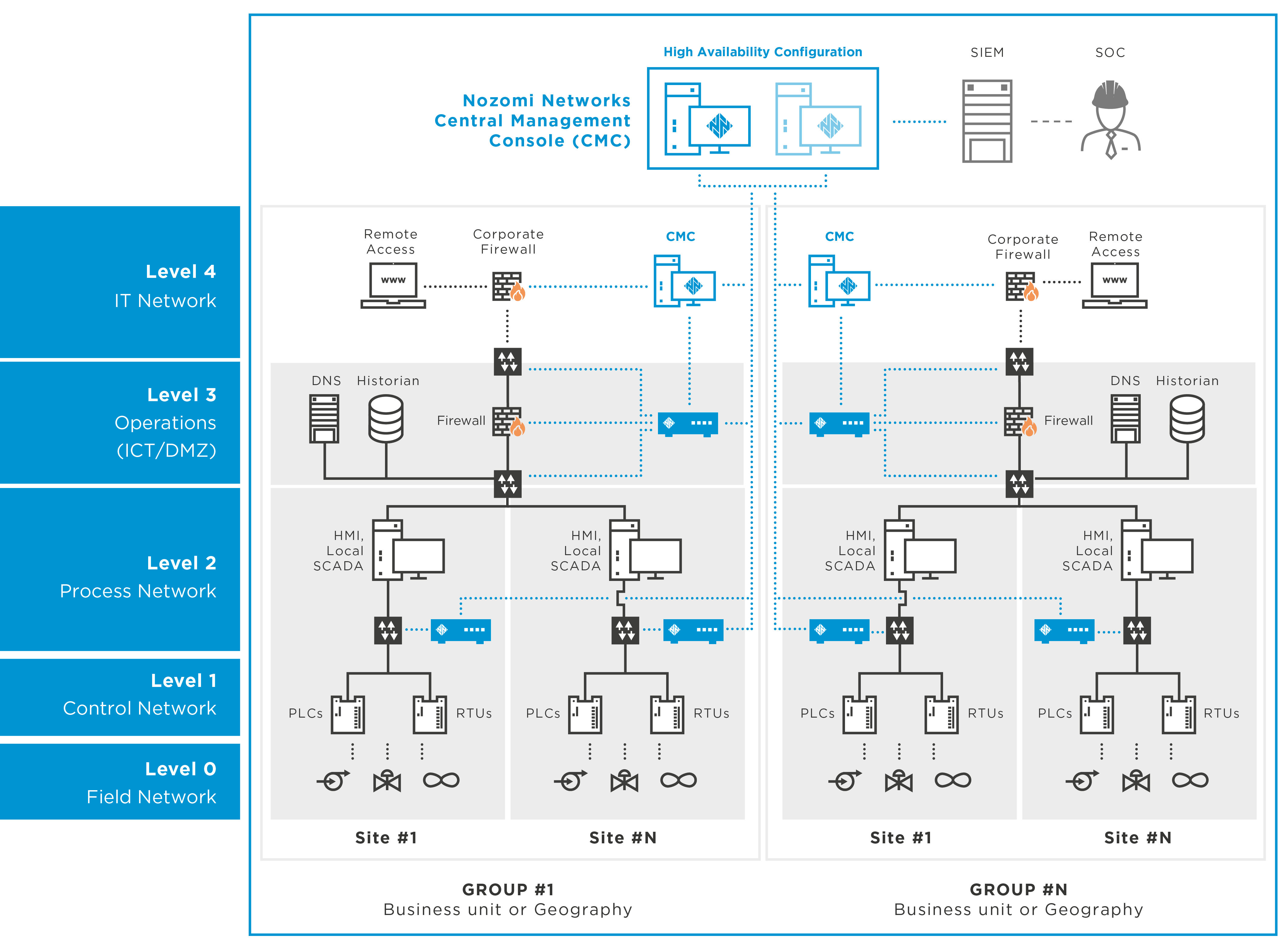
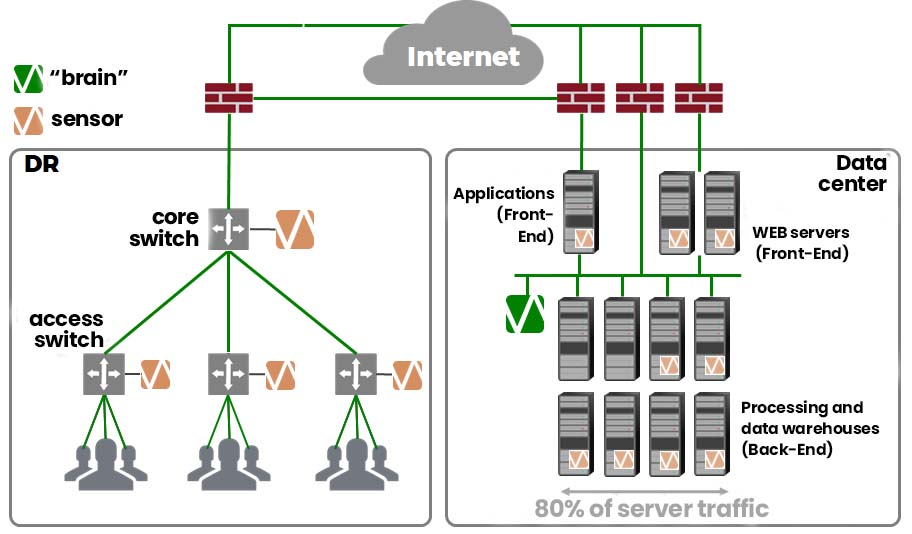
Protect your virtual environment from attacks by means of machine learning and AI-based solutions
We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Why work with the Smart Com team?
Partners in the field of technology
We work with global leaders in specific technology segments.